Unlocking The Power Of The Unix Finger Command
The Unix finger command is an essential tool for system administrators and users alike, offering a glimpse into the lives of users logged into a Unix system. Whether you're managing a network of servers or simply curious about who else is online, this command can provide valuable information at your fingertips. From user details to their current status, the finger command can help streamline communication and enhance collaboration in a multi-user environment.
In the world of Unix, where command-line interfaces reign supreme, understanding and utilizing the finger command can significantly improve the way you interact with other users. It’s not just about retrieving information; it’s about fostering a sense of community among users and ensuring that everyone is on the same page. With the right knowledge, you can leverage this command to monitor activities, check user availability, and even troubleshoot issues that may arise in a shared environment.
As we delve deeper into the nuances of the Unix finger command, we will explore its various functionalities, use cases, and best practices. By the end of this article, you will be equipped with the knowledge to harness the full potential of the finger command, making your Unix experience more efficient and productive. Let’s embark on this journey of discovery and unlock the secrets of the Unix finger command!
Read also:Bellossom The Vibrant Evolution Of Natures Charm
What is the Unix Finger Command?
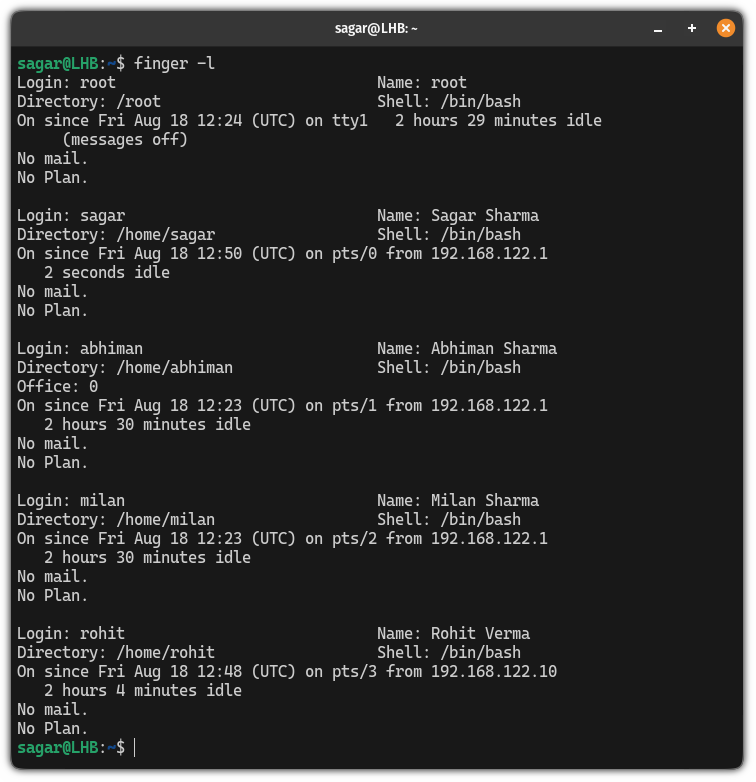
The Unix finger command is a utility that allows users to retrieve information about other users on the same system or network. By executing this command, a user can view details such as login names, real names, terminal locations, idle times, and other pertinent information related to system users. This command is particularly useful in multi-user environments, where collaboration and communication are key to success.
How Does the Finger Command Work?
When a user types the finger command in the terminal, the system retrieves user information from the user database (usually /etc/passwd) and displays it in a human-readable format. The basic syntax of the command is as follows:
finger [options] [usernames]
By default, if no usernames are specified, the command will display information about all currently logged-in users. Users can also utilize various options to filter the output or obtain specific information. For instance, the command can be customized to show only certain fields or to display information about remote users.
What Information Can You Obtain Using the Finger Command?
When using the Unix finger command, you can expect to gather the following information:
- Login name: The username of the individual.
- Real name: The full name of the user, if available.
- Terminal: The terminal or device the user is connected to.
- Idle time: Duration since the user last interacted with the terminal.
- Login time: The date and time the user logged into the system.
- Home directory: The path to the user's home directory.
- Mail status: Information regarding unread mail, if applicable.
How to Use the Finger Command Effectively?
To make the most of the Unix finger command, you should familiarize yourself with its various options. Some common options include:
- -l: Displays a longer format with more detailed information.
- -m: Matches the username case-insensitively.
- -s: Short format that provides less information.
By combining these options, you can tailor the output to your specific needs, making it easier to find relevant information quickly. Moreover, understanding the context in which you are using the finger command can help you avoid unnecessary output and focus on what matters most.
Read also:The Ultimate Guide To Lord Of The Lost An Indepth Analysis
Are There Any Alternatives to the Finger Command?
While the Unix finger command is a powerful tool for user information retrieval, there are alternative commands that offer similar functionalities. Some of these include:
- who: Displays who is currently logged into the system.
- w: Provides information about users and their current activity.
- users: Lists the usernames of users currently logged in.
Each of these commands has its strengths and weaknesses, so it is essential to choose the one that best fits your needs based on the information you seek.
Can the Finger Command Be Restricted for Security Reasons?
In some cases, administrators may choose to restrict the use of the finger command for security reasons. Displaying user information can pose privacy concerns, especially in sensitive environments. To limit access, administrators can modify the configuration files or disable the service altogether. It’s crucial to balance the need for user information with privacy considerations, ensuring that users feel safe while using the system.
What Are Some Common Use Cases for the Finger Command?
The Unix finger command can be employed in various scenarios, including:
- Checking user availability: Quickly determine if a colleague is online before sending a message.
- Monitoring system activity: Keep track of who is logged in and their activity status.
- Managing user accounts: Retrieve information about user accounts for administrative purposes.
These use cases illustrate the versatility of the finger command, making it an indispensable tool for anyone working in a Unix environment.
Conclusion: Why Mastering the Finger Command Matters?
In conclusion, the Unix finger command is a valuable resource for anyone navigating the complexities of multi-user systems. By understanding its functionalities, options, and practical applications, you can enhance your productivity and foster better communication within your network. As you explore the intricacies of this command, remember to balance the benefits of user visibility with privacy considerations, ensuring a healthy and collaborative environment for all users.
Article Recommendations
:max_bytes(150000):strip_icc()/linux-finger-command-ee31cf0771964565af41a35a68cd620b.jpg)